You Do Not Have Permission To Access The Specified Resource Security Group
You can then create a review on that group to ensure those who still need access should have.
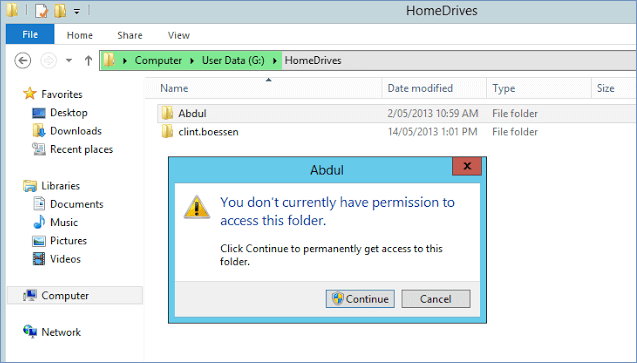
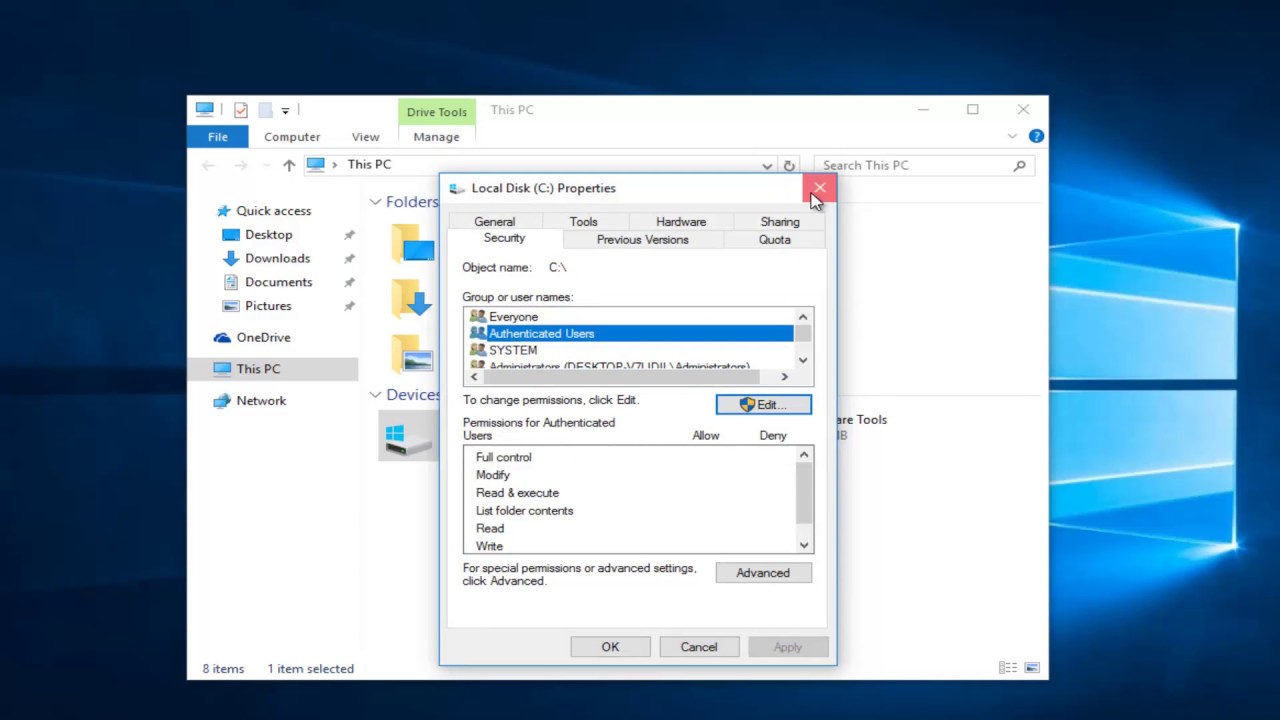
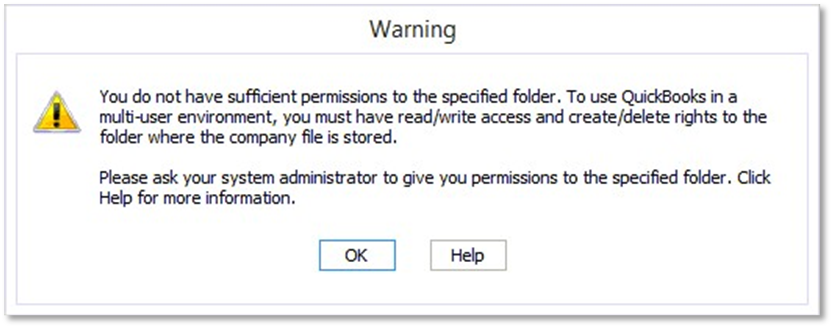
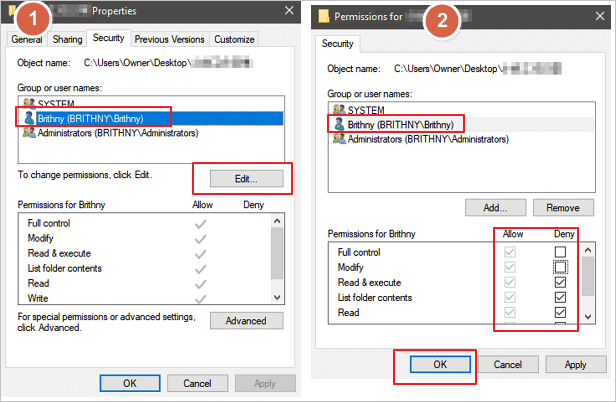
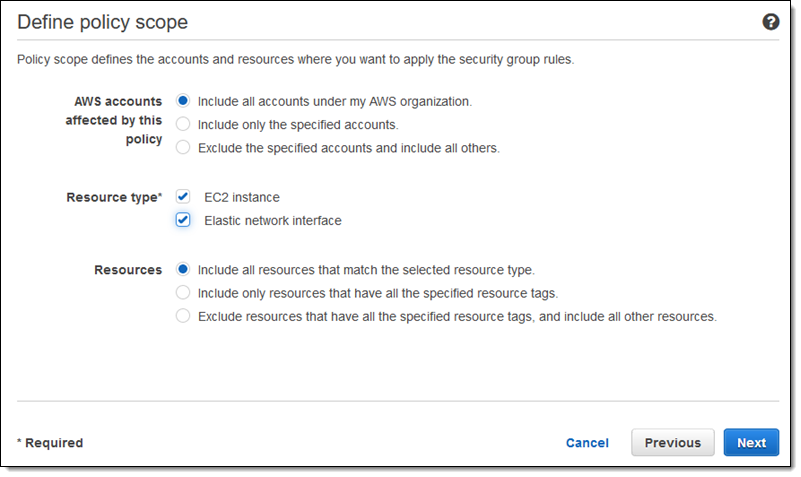
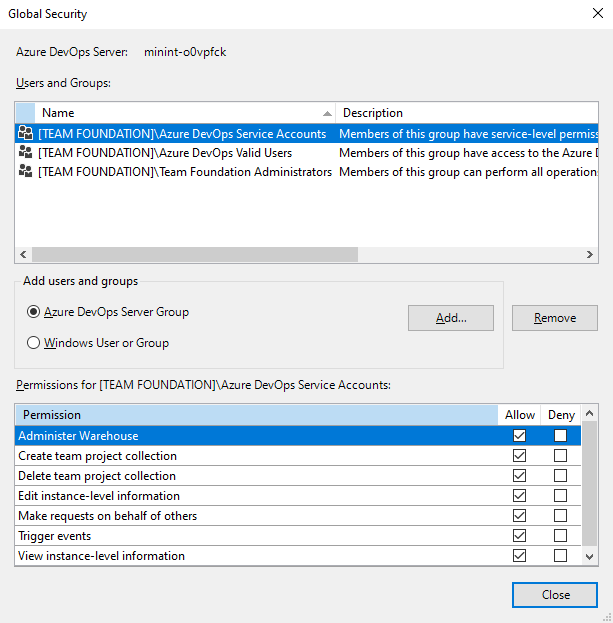
You do not have permission to access the specified resource security group. I unable to create new resource group. Select the user or group from the list and then click add. To assign permissions to delegates click add under the appropriate permission. Most permissions are granted through built in security groups as described in permissions and access.
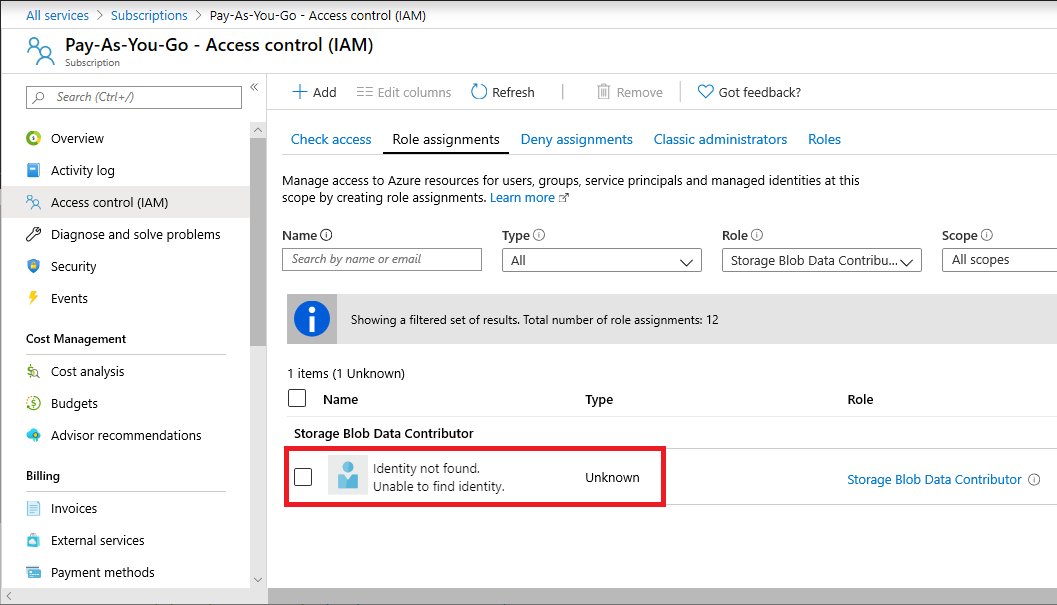
This condition ensures that access will be denied to the specified group management actions when the user making the call is not included in the list. If you want to grant create resource group permission to that account we can set it here. It is a by design behavior because the owner permission works for that resource group not for the subscription. A dialog box appears that lists the users or groups that can have the permission assigned to them.
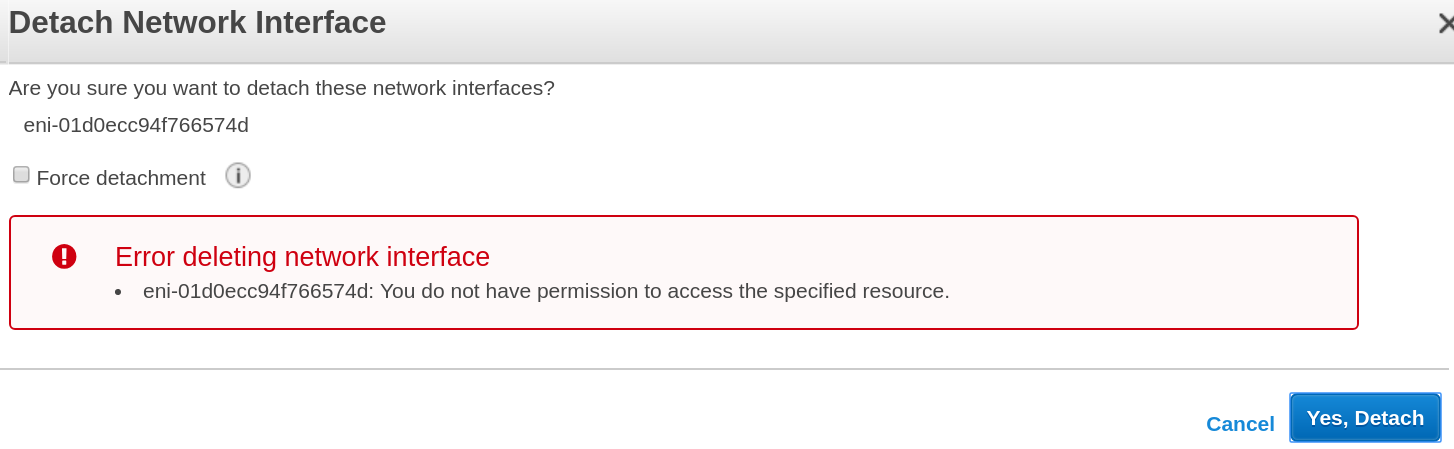
You can create rules for dynamic membership on security groups or microsoft 365 groups but what if the hr data is not in azure ad or if users still need access after leaving the group to train their replacement. Find the relevant item device or object e g if you see elb go to load balancing load balancers. Other than the above but not suitable for the qiita community violation of guidelines aws でネットワークインターフェースの削除で you do not have permission to access the specified resource. You do not have permission to access the specified resource what do you do to delete a network interface in aws when you get this error.
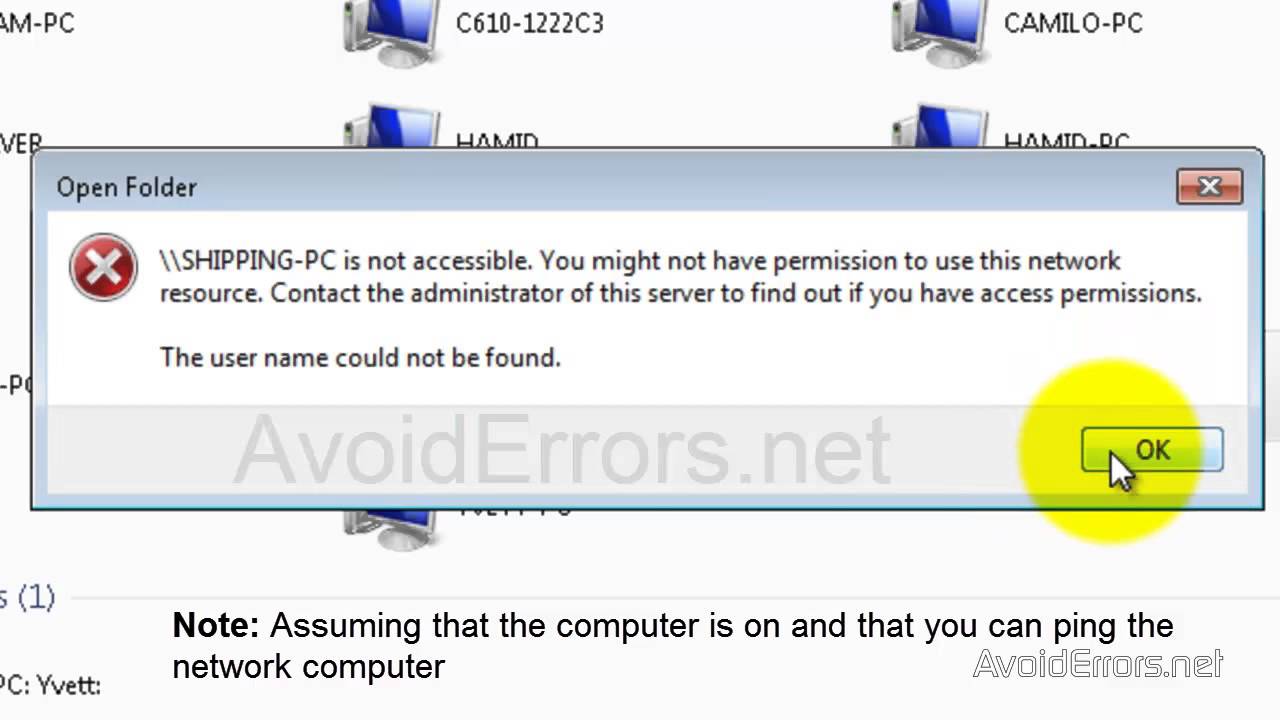
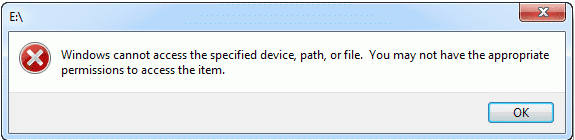
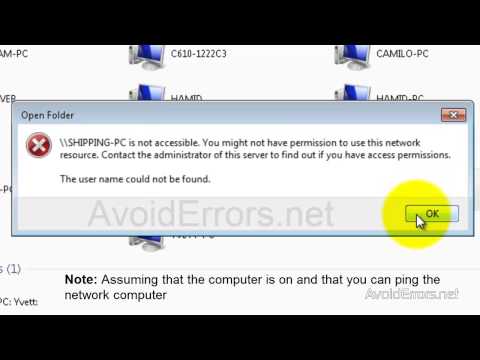
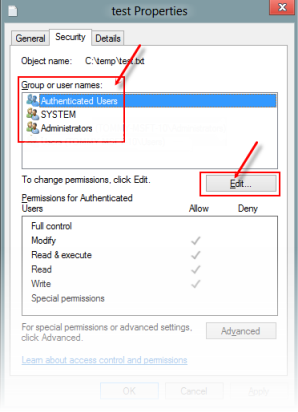
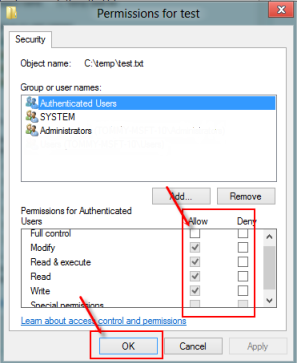
To access the resources you manage in azure devops such as your code builds and work tracking you must have permissions for those specific resources. I m using one as a file server. My issue is i have shared the c drive on this file server giving everyone full control but from the workstations when i click onto network and double click onto the file server name server i receive the below error. Option 1 will remove denied user s access to the group or application being reviewed they will still be able to sign in to the tenant.
The delegate can open the mailbox and do anything except send messages. When automation is not possible. If there was a mistake or if an admin decides to re enable one s access they can do so within 30 days after the user has been disabled. Because this explicitly denies permission it overrides the previous block that allowed those users to call the actions.
Option 2 will block the denied users from signing in to the tenant regardless if they have access to other resources.